
The Digital Extortionists: Understanding the Rise of Ransomware Gangs and Cryptocurrency Demands
Introduction
In the intricate and often perilous landscape of modern cybercrime, no threat looms larger or strikes with more chilling efficiency than ransomware. Once a niche tool for petty criminals, ransomware has metastasized into a multi-billion dollar industry dominated by sophisticated criminal enterprises. These groups, often operating with impunity from safe havens, have perfected the art of digital extortion, holding organizations hostage by encrypting their data and demanding exorbitant payments, almost exclusively in cryptocurrencies like Bitcoin.
This article will explore the evolution of ransomware, the sophisticated business models behind these gangs, their preferred methods of attack, and the crucial role cryptocurrency plays in facilitating their illicit operations. We will delve into how these digital extortionists have become a national security threat, crippling critical infrastructure and draining billions from the global economy.
From Nuisance to National Threat: The Evolution of Ransomware
The concept of encrypting data and demanding payment isn’t new, but the widespread availability of robust encryption, anonymity-enhancing cryptocurrencies, and easily exploitable network vulnerabilities has fueled its explosive growth.
Early ransomware, like the AIDS Trojan in 1989, was rudimentary. However, the game changed dramatically around 2013-2014 with the emergence of crypto-ransomware like CryptoLocker, which used strong, practically unbreakable encryption. The 2017 WannaCry and NotPetya attacks, while not solely focused on financial gain, demonstrated the devastating potential for rapid, widespread disruption.
Today’s ransomware is far more sophisticated, moving beyond simple encryption to a multi-stage extortion strategy:
Initial Access: Gaining entry via phishing, exploiting unpatched software vulnerabilities (e.g., in VPNs, RDP), or buying access from initial access brokers.
Network Reconnaissance & Lateral Movement: Mapping the victim’s network, identifying critical systems and data, and spreading their foothold.
Data Exfiltration (Double Extortion): Stealing sensitive data before encryption. This allows for a “double extortion” threat: pay the ransom, or your data will be encrypted and publicly leaked.
Encryption: Encrypting crucial files and systems, making them inaccessible.
Ransom Demand: Presenting a ransom note, typically demanding cryptocurrency and setting a deadline.
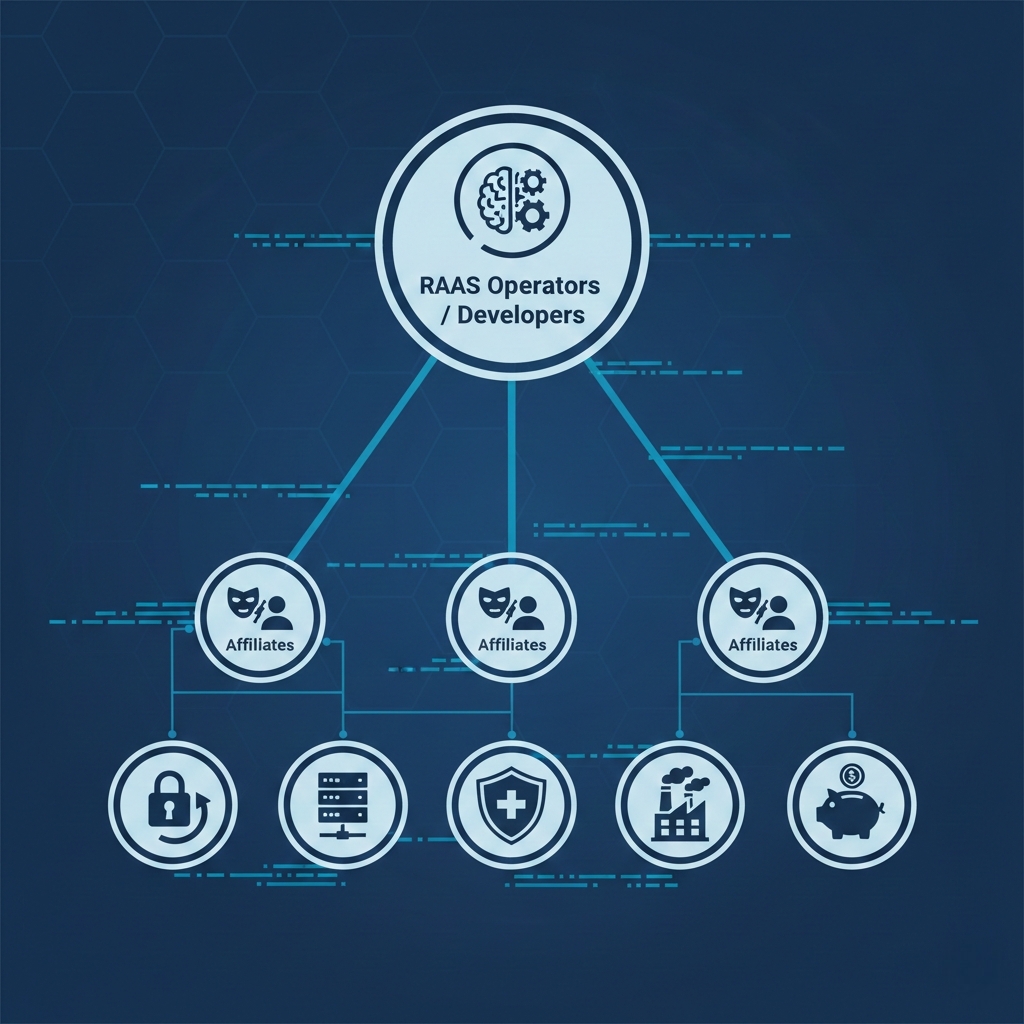
The Business of Extortion: Ransomware-as-a-Service (RaaS)
One of the most significant factors behind the proliferation of ransomware is the Ransomware-as-a-Service (RaaS) model. This is a subscription-based or profit-sharing scheme where core development teams create and maintain the ransomware code and infrastructure, while “affiliates” (other cybercriminals) carry out the actual attacks.
RaaS Operators (Developers): They develop the malware, manage command-and-control servers, and handle negotiations and payment processing infrastructure. They take a percentage (often 10-30%) of successful ransoms.
Affiliates: These are the “foot soldiers” who gain initial access to victim networks, deploy the ransomware, and often engage in the initial negotiation. They keep the larger share of the ransom.
This division of labor has lowered the barrier to entry for cybercriminals, allowing individuals with limited technical skills to execute highly damaging attacks, while highly skilled developers can focus on innovation. Notorious RaaS groups include Conti, LockBit, REvil (Sodinokibi), DarkSide, and BlackCat (ALPHV).
Why Cryptocurrency? The Indispensable Role of Digital Money
Cryptocurrency, particularly Bitcoin, is not just a preference but an essential component of the modern ransomware ecosystem. Its pseudo-anonymous and decentralized nature offers several advantages to criminals:
Pseudo-Anonymity: While blockchain transactions are publicly visible, linking a wallet address to a real-world identity is challenging without extensive forensic work or a slip-up by the criminals. This provides a crucial layer of obfuscation.
Global Reach & Immutability: Cryptocurrency transcends national borders and traditional banking systems. Once a transaction is confirmed on the blockchain, it is irreversible, providing criminals with finality of payment.
Speed: Transactions can be settled quickly, allowing for rapid payment and minimizing the time victims have to consider alternatives.
Limited Regulatory Oversight: Compared to traditional banking, the cryptocurrency ecosystem historically had fewer “Know Your Customer” (KYC) and Anti-Money Laundering (AML) regulations, though this is changing rapidly.
The Role of Monero
While Bitcoin remains dominant, some ransomware gangs are increasingly demanding Monero (XMR). Monero offers enhanced privacy features that make it even more difficult to trace than Bitcoin, which is why it’s gaining favor among sophisticated actors seeking maximum anonymity.
High-Profile Attacks: When Ransomware Becomes Headline News
The impact of ransomware is no longer confined to IT departments. Major attacks have become international incidents:
Colonial Pipeline (May 2021): The DarkSide ransomware gang disrupted the largest fuel pipeline in the US, leading to fuel shortages and panic buying. The company paid approximately $4.4 million in Bitcoin (though the FBI later recovered a portion). This attack highlighted the vulnerability of critical national infrastructure.
JBS (May 2021): The world’s largest meat processor was hit by the REvil gang, leading to significant disruptions in the global food supply chain. JBS paid $11 million in Bitcoin.
Kaseya VSA (July 2021): The REvil gang launched a massive supply chain attack via Kaseya’s IT management software, impacting hundreds of businesses worldwide. They initially demanded $70 million in Bitcoin for a universal decryptor.
These incidents underscore that ransomware is no longer just about data; it’s about disrupting economies, supply chains, and public confidence.
The Fight Back: Countering Digital Extortion
Governments and cybersecurity firms are escalating their efforts to combat ransomware:
Law Enforcement Action: International cooperation has led to the arrests of key ransomware operators and affiliates, and the seizure of infrastructure and cryptocurrency.
Sanctions: Governments, particularly the US Treasury, have sanctioned specific cryptocurrency mixing services and wallet addresses known to be associated with ransomware payments, making it harder for criminals to launder their funds.
Intelligence Sharing & Threat Prevention: Improved information sharing between public and private sectors helps in developing better defensive strategies and patching vulnerabilities.
Victim Support: Initiatives like the “No More Ransom” project provide free decryption tools for certain ransomware variants.
Conclusion: A Persistent and Evolving Threat
The rise of ransomware gangs, fueled by the efficiency and pseudo-anonymity of cryptocurrency, represents one of the most pressing cybersecurity challenges of our time. These groups are agile, innovative, and ruthless, constantly evolving their tactics to bypass defenses and maximize profits.
While significant strides are being made in tracking, disrupting, and prosecuting these digital extortionists, the threat remains persistent. For businesses and individuals alike, robust cybersecurity practices, regular data backups, and a healthy skepticism towards unsolicited digital communications are no longer optional—they are critical lines of defense in a world where your digital assets can be held hostage at any moment
